Introduction
Organizations are now experiencing a lot of pressure that concerns service delivery, customer satisfaction, reduced costs, and the reliability of the networks in the current technological age. When networks become more complex, configuring and managing them with manual inputs requires a lot of time and often involves mistakes. Organizations, therefore, need a solution that can be reliable and adaptable for the diverse networks in today’s world.
This is why we have the Cisco Network Services Orchestrator, more commonly referred to as the Cisco ‘NSO’. NSO is the next generation of logical network automation and orchestration systems that can be appropriate for the organization to handle the networks.
In this blog, we will explain Cisco NSO architecture, exploring its fundamental concepts, key components, and how they work together to deliver a robust and scalable network automation platform. We will also discuss the benefits and challenges of deploying NSO in real-world environments and provide insights into best practices for successful implementation.
But, before explaining the architecture of Cisco NSO in deep, we need to know what Cisco NSO actually is.
What is Cisco NSO?
Cisco NSO, or Cisco Network Services Orchestrator, is a powerful network automation platform designed to simplify the management and orchestration of complex, multi-vendor networks. It offers a single point of administration for configuring and managing network services in various devices, including routers, switches, firewalls, and load balancers.
NSO enables the network administrator to control and monitor a number of services in the network, such as routing, switching, and other security services. It supports multi-vendor environments and also offers real-time information on the network inventory, configuration, and troubleshooting. Cisco NSO minimizes the occurrence of manual errors, enhances the flexibility of a network, and shortens the time it takes to deliver a service, thus leading to increased network stability, security, and efficiency. You can consider Cisco NSO Training to master this technology.
Now that you have a basic understanding of Cisco NSO, let us move on to next section i.e., Cisco NSO architecture.
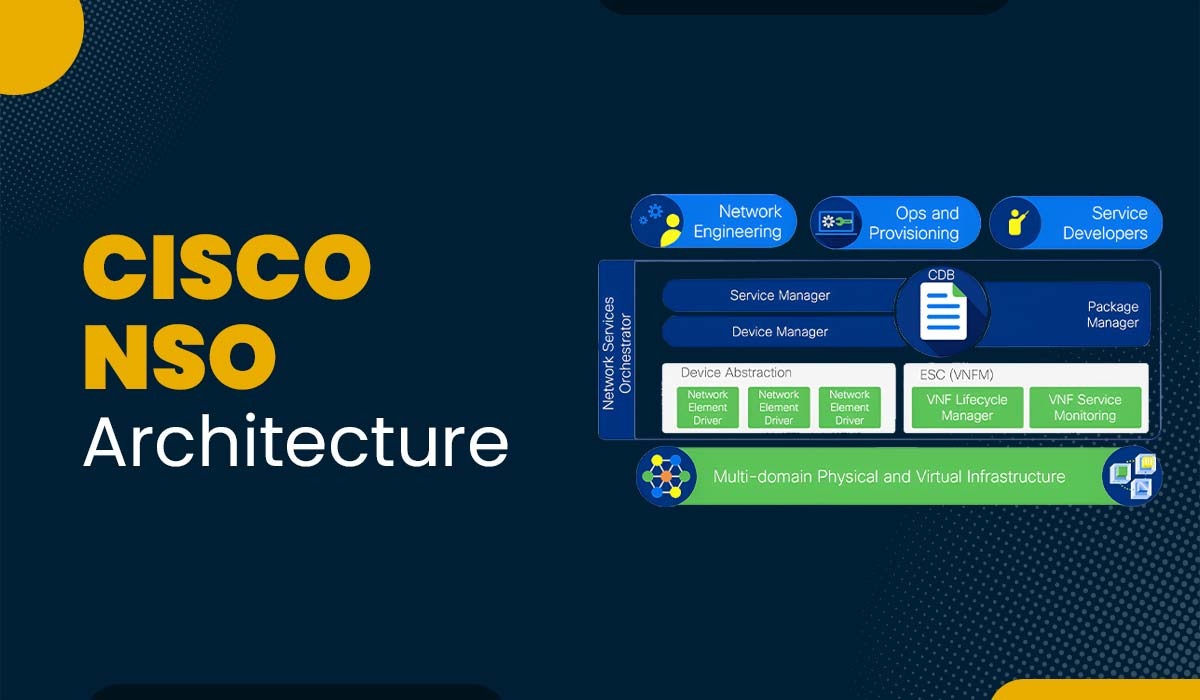
Cisco NSO Architecture
The Cisco NSO architecture is built around a model-driven approach, where network elements and services are represented by data models, enabling a high-level abstraction for easier management.
Let’s break down the architecture of NSO as depicted in the image.
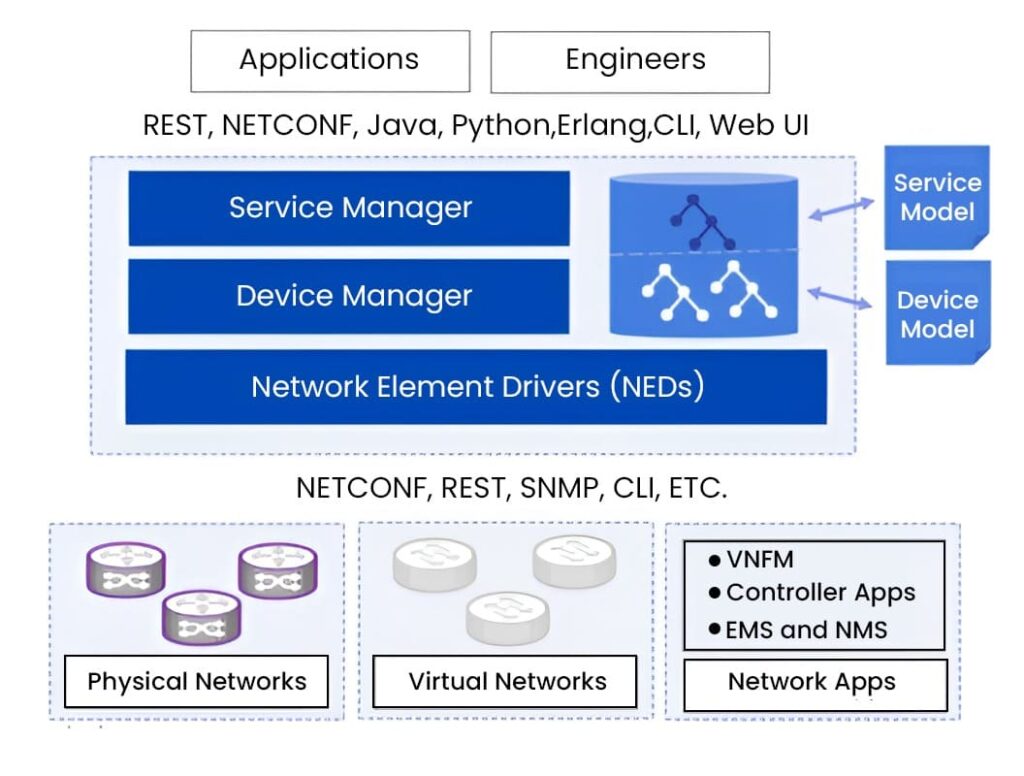
NSO operates through two primary layers: the device manager and the Service Manager. Although each has a specific function, they are closely connected to a transactional engine and database.
Service Manager
The Device Manager could be described as the central hub with regard to dealing with devices in a precise and transactional manner. This means NSO ensures every change to device configurations is tracked and controlled, ensuring consistency and preventing unintended errors. Some key features of the Device Manager include:
- Fine-grained configuration commands: What NSO brings is the fine-tuning of particular device parameters where one can modify or tune certain aspects of the device without affecting others.
- Bidirectional device configuration synchronization: NSO will always keep on synchronizing the current configurations on the devices with its own database and vice-versa in case there are any updates on the two databases.
- Device groups and templates: According to NSO, grouping should be done according to the roles and configurations because of better management of similar devices. Templates can be created to define standard configurations for groups of devices, simplifying deployment and configuration.
- Compliance reporting: NSO provides detailed reports on device configuration compliance, which assist the network administrator in determining which device configurations may violate the recommended standards or set policies.
On the other hand, the Service Manager allows operators to configure high-level network parameters that cannot be configured at a device level or may require extensive configuration to implement. The Service Manager also plays the role of an abstraction layer that hides multiple network settings.
For example, an operator may assign VLAN for the whole network in a given region through the Service Manager. The Service Manager can then intelligently compute the required configuration changes to all the devices in the network and then apply the changes as needed.
A Service Manager can create, modify, and delete services, and each of these tasks involves a process. It has a flexible mapping layer that enables the network engineer to determine how a given service can be run across the network in a way that is easy to understand.
Configuration Database
At the core of NSO’s functionality is the Configuration Database (CDB). This dedicated storage system stores all the configurations and always remains synchronized with the actual network device configurations. NSO uses an audit and reconciliation mechanism to assure configuration consistency and to synchronize the configuration with actual devices to ensure the integrity of data. Also, the CDB always stores runtime relationships between service instances and corresponding device configurations, which gives a real view of the network state.
Network Element Drivers
NSO uses Network Element Drivers or NEDs for making communications with devices. NEDs are not rigid, hard-coded adapters. However, the device interface is more abstract and is modelled using a data modelling language known as YANG. NSO can import these YANG models and directly generate the needed commands or operations from them.
This also includes support for legacy configuration interfaces such as device CLIs making NSO fully compatible with the latest as well as the old devices. This model-driven approach ensures adaptability as new commands are introduced. Implementing new commands in NEDs entails only extending YANG data models; thus, there is no complicated programming to be done.
Additional tools in NSO are also available that can simulate the configuration aspects of a given network. The netsim tool is able to emulate management interfaces that are already in existence such as the Cisco CLI and NETCONF and enables services to be tested and developed in a controlled environment. This feature is extremely useful for service development and testing, which enables a simple transition to actual network models.
Let us now discuss some of the advantages of using Cisco NSO architecture.
Advantages of Cisco NSO Architecture
Below, we have discussed some of the advantages that the architecture of Cisco NSO offers.
- Model-driven Approach: NSO leverages data models to represent network elements and services, simplifying complex configurations and making management more intuitive.
- Centralized Control: NSO provides centralized management of services from several vendors and domains, thus eliminating undue complications arising from the centralization of different network services.
- Automation: Some of the tasks that NSO performs include device provisioning, service deployment, and troubleshooting, which would require the intervention of network engineers but are automated, hence saving a lot of time and energy.
- Scalability and Resilience: NSO is designed for large and complex networks so that it can support today’s network needs in terms of size and dynamics.
- Open Standards Compliance: NSO, as a product, complies with various standard communication protocols varying from NETCONF, REST, and SNMP to interconnect with a vast number of different network devices and applications.
Before we discuss some of the best practices for implementing Cisco NSO’s architecture, let’s first understand the challenges associated with Deploying it in a real-world environment.
Challenges of Deploying Cisco NSO Architecture in Real-World Environments
Below, we have discussed some of the common challenges that network engineers and administrators might face:
Challenges in Planning and Design
- Complex Network Topology: Real-world networks are even more complicated and present a huge number of interconnected devices, services, and applications. These can create many challenges in the design and planning process of the NSO implementation.
- Inconsistent Network Configuration: Most networks do not have a well-defined structure, which makes it difficult to set the architecture for NSO.
- Lack of Standardization: There are often certain differences between devices and/or services as to how they should be configured. This makes it challenging to create a standardized architecture for NSO.
Challenges in Integration and Interoperability
- Integration with Legacy Systems: Most networks have outdated networks that are not compatible with NSO. Successively, integrating these systems with NSO may be complex, in particular, it may be necessary to develop new adapters or interfaces.
- Interoperability Issues: Making sure that NSO integrates seamlessly with other network management systems and tools can be a problem especially if these come from a variety of different vendors.
- Multi-Vendor Support: NSO needs to support devices and services from multiple vendors. One of the difficulties when implementing NSO is to make sure that NSO supports all the vendors required for the architecture and their correct configurations.
Challenges in YANG Modelling
- Complexity of YANG Models: While YANG models can be simple, such models can also be complex, and it could take deep knowledge to define and set appropriately.
- YANG Model Validation: Validating YANG models to determine whether the models developed are correct and complete can sometimes prove exhaustive and costly in terms of resources.
- YANG Model Updates: However, it becomes quite cumbersome to manage the YANG models within a network while keeping them up-to-date due to the dynamic network environment that is always being developed.
Challenges in Deployment and Operations
- Deployment Complexity: NSO integration can pose a number of difficulties based on the setting in consideration and is therefore needed to carry out a proper implementation plan.
- Training and Support: All in all, it may become an immensely challenging task to adequately train and support network engineers and administrators, given the fact that there are some organizations that may not be financially well endowed.
- Ongoing Maintenance: Updating and maintaining NSO is a technical process, it may be a difficult task to do, especially if the environment is dynamic.
Challenges in Security and Compliance
- Security Risks: If the NSO is not set up or managed correctly, it can add new security risks. One of the stakeholders’ major concerns could be to ensure that the NSO is safe from other users/employees and free from any organizational security policies and regulations.
- Compliance Issues: It might be difficult to guarantee that NSO meets the necessary regulatory standards, especially when operating in specialized areas.
- Audit and Compliance: Ensuring that NSO contains sufficient audit and compliance capacities can be challenging, especially in the tough auditing context.
Now, let us discuss the best practices that you can follow in order to successfully implement the architecture of Cisco NSO.
Best Practices for Successful Implementation of Cisco NSO Architecture
Substantial planning, execution, and management are needed in order to deploy the architecture of Cisco NSO successfully. Below, we have discussed some of the best practices to help you achieve a successful implementation:
Pre-Implementation Planning
- Define Clear Objectives: Determine the concrete network challenges that you would like to address through NSO, such as simplifying network management or enhancing service provision.
- Assess Your Network: Assess the current network infrastructure, gadgets, and services in place so that one can determine the right approach to implementing NSO.
- Develop a Project Plan: Develop a strategy, develop a precise project schedule, and define objectives to guide the project’s implementation process.
NSO Architecture Design
- Design a Scalable Architecture: It is important that your NSO architecture should cater to the expansion of your network in that it should have capacities for the additional resources that it would need in the future.
- Use a Modular Approach: Divide your network into logical modules or domains to simplify management and enable easier troubleshooting.
- Define YANG Models: Develop YANG models that will represent your network data such as devices, services, and the relationships between them.
Implementation and Configuration
- Start with a Pilot Project: It is advisable to adopt the NSO in an organization as a pilot study to avoid a large-scale implementation with numerous and costly mistakes.
- Configure Devices and Services: Carefully configure devices and services in NSO, ensuring accuracy and consistency with your existing network configuration.
- Use Templates and Profiles: Make use of templates as well as profiles to streamline configuration and reduce the risk of human error.
Ongoing Management and Monitoring
- Establish Monitoring and Logging: Monitoring, as well as logging systems, should be put in place to track the performance of NSO and also detect problems that may be affecting your network and find ways of making improvements.
- Develop a Change Management Process: Create a change management process to ensure that changes to your network are properly documented, tested, and deployed.
- Provide Ongoing Training and Support: Provide formal and informal training and coaching to network engineers and administrators to help them feel comfortable working with NSO and effectively troubleshoot issues.
Best Practices for YANG Modelling
- Use Standardized YANG Models: Whenever possible, apply standardized YANG models to prevent situations where disparate players within the vendor community and elsewhere develop their own YANG-related models, making integration with the technology more complicated.
- Keep YANG Models Up to Date: Make periodic changes to your YANG models to augment your network architecture, devices, and services.
- Use YANG Model Validation: Validate your YANG models to ensure that they conform to a standard and avoid unnecessary mistakes.
Security and Compliance
- Implement Role-Based Access Control: Implement RBAC with regards to NSO so that only those with permission are allowed to adjust the settings.
- Use Encryption and Authentication: Security should be enhanced by allowing encryption and authentication of the NSO’s communication and information.
- Comply with Regulatory Requirements: Make sure that the NSO that you plan to implement does not violate any of the current laws and regulations, especially data protection laws.
Frequently Asked Questions
Q1. What is the Cisco NSO?
Cisco NSO is an automation platform that simplifies network management by using models to automate device configuration and orchestration.
Q2. What is the structure of the NSO?
NSO’s structure consists of a central controller, network devices, and a database containing models for representing network services and configurations.
Q3. What are the benefits of Cisco NSO?
Cisco NSO benefits include simplified network management, faster service deployment, reduced errors, improved agility, and increased network efficiency.
Q4. What is NSO orchestration?
NSO orchestration uses models to automate the configuration, deployment, and management of network services and devices, ensuring consistency and reducing manual errors.
Conclusion
Cisco NSO (Network Services Orchestrator) architecture is a widely popular automation platform that assists networks to become more adaptive, responsive, and protected. It simplifies the configuration of the network, thereby minimizing the number of errors that may happen. These characteristics make it relatively simple for NSO to be installed in existing systems or to ensure that your network is ready for the changes the future may bring. Whether you are a network engineer, architect, or administrator, this blog assists in laying down the knowledge about the Cisco NSO architecture and how it can transform the existing network management.