Introduction
OSI model or Open Systems Interconnection model serves as a framework that explains the process of information transfer, i.e., from one computer’s software application to another computer through a medium. It was created by the International Organization for Standardization (ISO) in 1984. It is now widely acknowledged as an architecture model for inter-computer communication. In this blog, we will explain what the OSI model is, along with the different layers associated with it.
Let’s begin by explaining the OSI model. You can learn OSI model in Detail with PyNet Labs’ CCNA Course.
What is OSI model ?
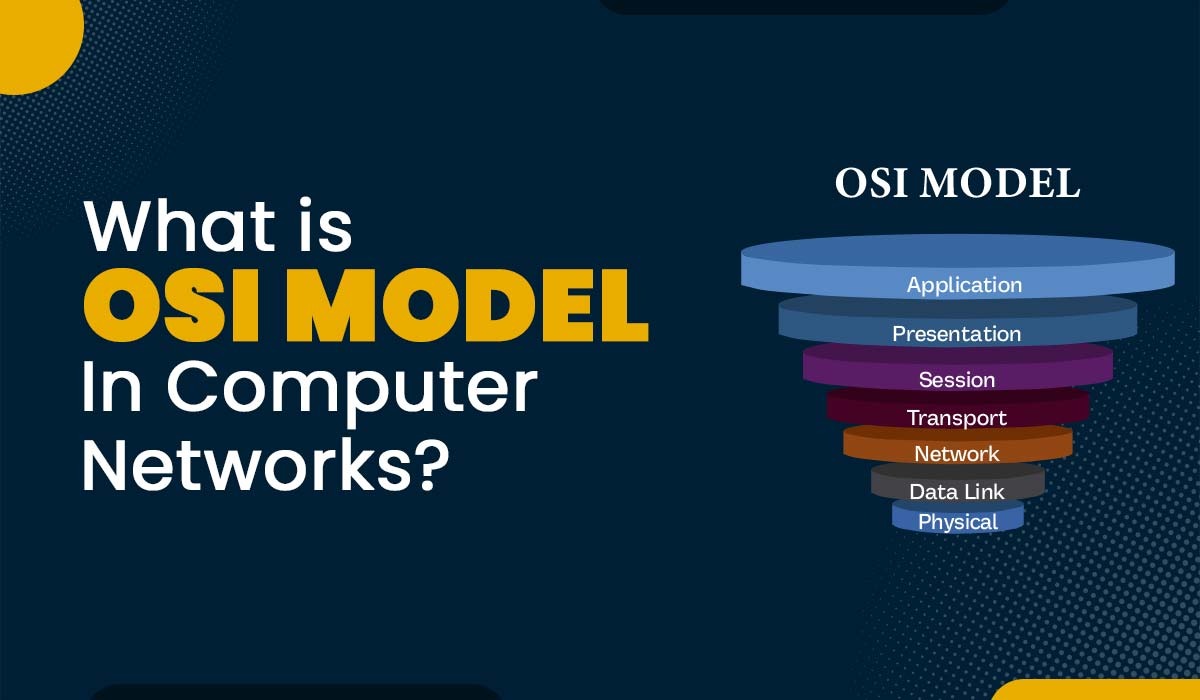
OSI model is nothing but an architecture model that assists in breaking down the task of data communication into seven layers. Each layer has its role and further interacts with the adjacent layers. This model works in a way that describes how various network devices and protocols work with one another.
The OSI model is divided into seven layers. These are:
- Application Layer
- Presentation Layer
- Session Layer
- Transport Layer
- Network Layer
- Data Link Layer
- Physical Layer
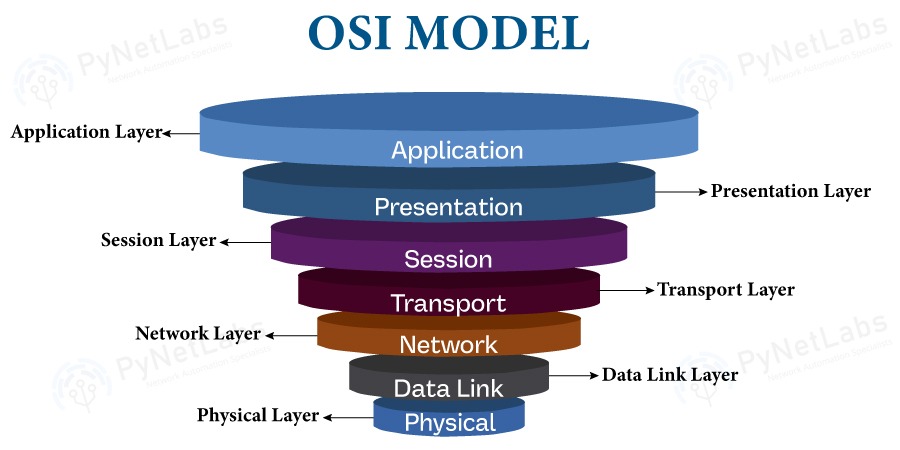
Inside this model, each layer works on certain network functions and further communicates with both layers, i.e., one above it and the other below it. When we talk about the upper layers (application, presentation, and session), also known as the software layer, we focus on issues related to the applications themselves, such as user interface design, data formatting, and encryption techniques. On the other hand, when we talk about the lower layers (network, data link, and physical), also known as the physical layer, we focus on issues such as error control processes and transmission mediums.
In the middle is the heart of the OSI model, i.e., the transport layer.
Before explaining each layer in detail, let’s first understand the purpose of the OSI model.
Purpose of OSI Model
The primary goal of the OSI model is to promote compatibility between network devices and software applications. By adopting the OSI model as a standard reference, network engineers and developers can guarantee collaboration and integration, across platforms and systems.
There are advantages associated with the OSI model. Some of these are:
- It streamlines the network design process by breaking it down into segments.
- It facilitates the development and testing of network components.
- It allows for troubleshooting and problem identification by pinpointing faulty layers.
Let’s now discuss each layer in detail.
The 7 Layers of OSI Model
This section will explain the different layers in the OSI model, along with some practical examples.
Application Layer
At the top of the OSI model, we have an application layer. This layer generally deals with the end users and serves as a bridge between them and various other applications such as web browsers, email clients, and file transfer protocols. It further plays a significant role in allowing communication by defining protocols such as HTTP, SMTP, FTP, etc.
Function of Application Layer
Below, we have discussed some of the key functions performed by the application layer.
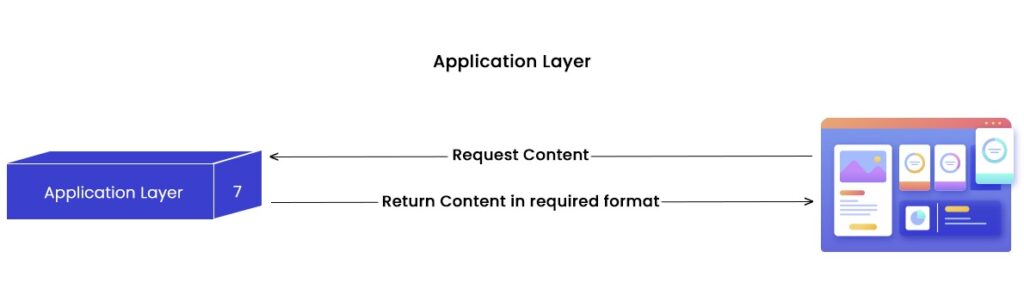
- Identifying communication partners: Here, the application layer assists in determining the parties that are involved in a communication process and further verifies their availability.
- Determining resource availability: It verifies that all the network resources required to communicate are available.
- Synchronizing communication: The application layer is the head that manages and synchronizes interactions between different applications.
Presentation Layer
When we talk about the presentation layer, it is simply responsible for translating the data between the application layer that is above it and the lower layers. It also ensures the compatibility format of the data for both the sender as well as receiver applications. Apart from that, it also handles data compression, encryption, and decryption.
Function of Presentation Layer
Below, we have explained some of the main functions of the presentation layer.
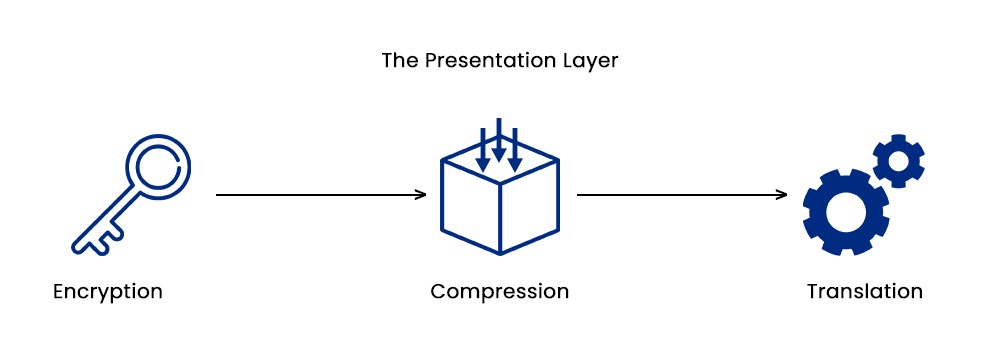
- Data Translation: In data translation, the presentation layer simply converts data from one format to another, whichever is suitable for the upper and lower layers. An example is converting ASCII to EBCDIC or binary text.
- Data Compression: When we talk about data compression, the presentation layer reduces the data size to save bandwidth and storage space.
- Data Encryption: In order to maintain the integrity as well as privacy of the data, the presentation layer encrypts it.
Session Layer
The session layer assists in establishing, maintaining, and terminating sessions between different applications. It is a logical connection responsible for allowing continuous data exchange between two applications. Apart from that, it also helps manage authentication, authorization, and synchronization.
Functions of Sessions Layer
Some of the important functions of the session layer are:
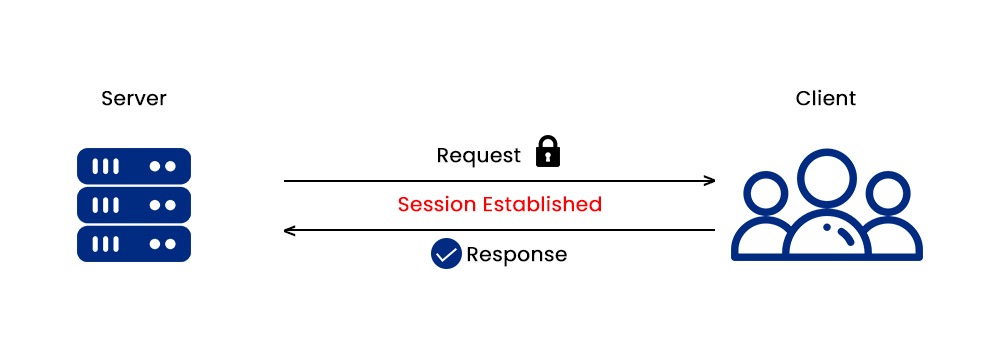
- Session Establishment: In session establishment, the session layer simply creates sessions between applications by exchanging control information. These include usernames, passwords, and session IDs.
- Session Maintenance: The session layer also assists in monitoring and controlling the sessions. This is done by sending acknowledgements, checkpoints, and timeouts.
- Session termination: In the end, the session layer ends the session by releasing resources and closing connections.
Transport Layer
The transport layer assists in providing reliable and efficient data transfer between two devices within a network. It also ensures that the data that is delivered must be without errors, loss, or duplication. Apart from that, it is also responsible for regulating the flow of data in order to avoid congestion or overload.
TCP and UDP are the most important protocols that are used in the transport layer.
Function of Transport Layer
Below, we have explained some of the functions of the transport layer.
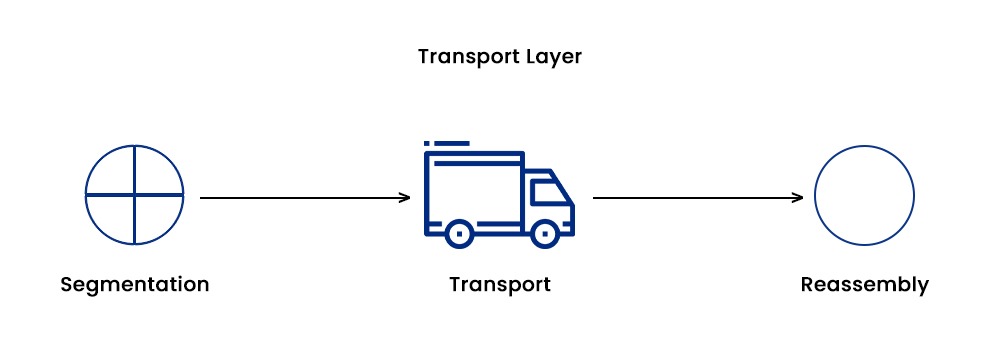
- Segmentation and Reassembly: In this case, the transport layer simply divides the data into small segments that can further be transmitted over the network. It also assists in reassembling the segments at the destination device.
- Error Control: The transport layer is responsible for detecting and correcting errors in the data with the help of checksums, acknowledgements, and retransmissions.
- Flow Control: In the end, the transport layer controls the rate at which the data is transmitted by using windowing, buffering, and many congestion avoidance techniques available.
Network Layer
The network layer assists in routing the packets from one device to another in a network. It is also responsible for determining the best path for the packets based on various factors such as distance, cost, and traffic. Apart from that, the network layer also handles addressing, fragmentation, and packet switching.
Function of Network Layer
Now, let’s discuss some of the crucial functions of the network Layer.
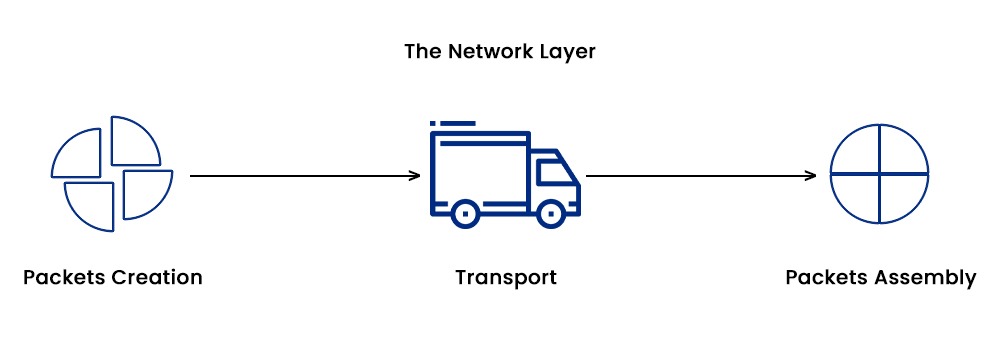
- Logical Addressing: In this, the network layer simply assigns logical addresses, such as IP addresses, to a network device in a network. It also maps logical addresses to physical addresses, such as MAC addresses, using protocols such as ARP and RARP.
- Routing: It is the work of the network layer to decide the best path for the packet using algorithms such as Dijkstra’s and Bellman-Ford.
- Fragmentation: Fragmentation simply means splitting large packets into small segments that can fit the maximum transmission unit (MTU) of the underlying network. Here, the network layer also comes into action.
- Packet Switching: The network layer is also responsible for switching the packets from one network to another using devices such as routers and gateways.
Some of the common protocols of the network layer are IP, ICMP, ARP, and RARP.
Data Link Layer
The data link layer is used for the node-to-node delivery of data. It further defines the format of data and also assists in providing reliable and efficient communication between two devices. It is also responsible for handling access control, error detection, and correction.
The data link layer is further divided into two sub-layers. These are:
- Logical Link Control: LLC assists in providing services to the upper layers. These services include flow control, error control, and multiplexing.
- Media Access Control: MAC is the one that controls how devices access and share the physical medium, such as Ethernet, Wi-Fi, or Bluetooth.
Functions of Data Link Layer
Now, let’s discuss the different functions of the data link layer.
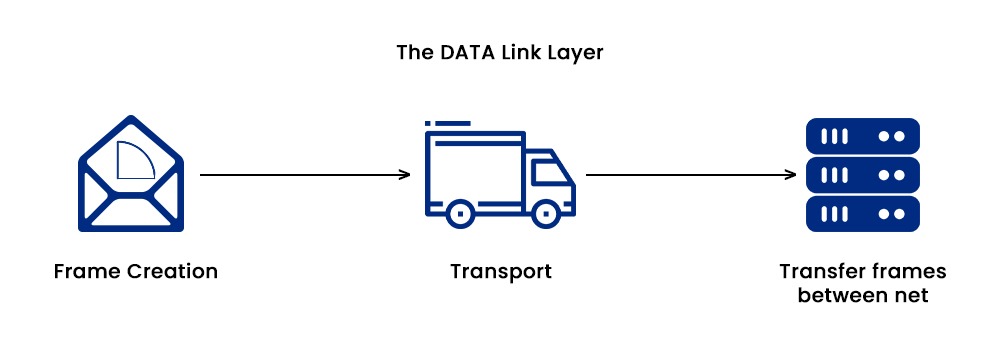
- Framing: The data link layer assists in dividing the data into frames that further contain a header, a payload, and a trailer. When we talk about the header, it contains information such as MAC addresses of the source and destination, frame types, and frame numbers. The trailer part contains a checksum for detecting the error.
- Error Detection: This layer helps in detecting the errors in the frames by using methods such as parity check, cyclic redundancy check (CRC), and checksum.
- Error Correction: The data link layer is also responsible for correcting the errors in the frames by using methods such as stop-and-wait, go-back-N, and selective repeat.
- Access Control: The data link layer regulates how devices access and share the physical medium by using methods such as CSMA/CD, CSMA/CA, and token passing.
Physical Layer
The last layer of the OSI model is the physical layer. It is closest to the physical medium and is responsible for transmitting as well as receiving individual bits from one device to another. Apart from that, the physical layer specifies the mechanical, electrical, and procedural characteristics of the physical medium.
Functions of Physical Layer
Below, we have explained some of the important functions of the physical layer.
- Bit Synchronization: This layer is responsible for the synchronization of bits by providing a clock signal that controls both sender and receiver devices.
- Bit Rate Control: It also defines the transmission rate by utilizing various methods. Some of these methods are modulation, encoding, and multiplexing.
- Physical Topologies: The physical layer assists in defining how devices are arranged in a network. This includes bus, ring, or mesh topology.
- Transmission Mode: One of the most important functions of the physical layer is defining how data flows between devices. This includes simplex, half-duplex, or full-duplex mode.
These are the 7 layers of OSI Model.
Importance of OSI Model
The following reasons explain why the OSI model is important:
- The OSI model assists in recognizing threats on the network as a whole. It facilitates the detection and troubleshooting of network problems by IT specialists at any point in the networking process. In addition, it is used to do asset inventories, classify organizational assets and data using model layers, and handle network vulnerabilities and security incidents according to the layers that are impacted by these problems.
- Cloud computing has become more and more popular in recent years, and many businesses are moving to the cloud due to its advantages. However, cloud systems might have security vulnerabilities such as malware insertion, data loss, unsecured APIs, and data breaches. When transitioning to the cloud, the OSI model is helpful because of its data-centric perspective, which helps in identifying the potential dangers to network data security associated with cloud adoption. It enables businesses to create more effective plans for selecting the kinds of cloud services to use, which can allay security worries.
- Since the OSI model places a high priority on network security, it can be used to cloud systems that are vulnerable to a variety of security problems, such as malware injection, data loss, unsecured APIs, and data breaches. The OSI model is flexible and may be used to create cloud infrastructure in a variety of ways. It does an inventory of the organization’s security assets and resources and is altered in a way that enhances the network security program.
- It has a data-centric perspective that helps in identifying the parts of the network where data security risks exist since it offers a framework for doing an inventory of the organization’s resources. It offers comprehensive details about every layer of the model, and this knowledge is essential for selecting the appropriate solutions that improve data visibility at the appropriate OSI layer. The OSI model is crucial for network compliance because it guarantees that controls are created in accordance with the data’s environment.
- Other frameworks and models, like the ITIL framework, can be combined with the OSI model. Organizations can create IT service management procedures that are more efficient and take into consideration the complexity of contemporary networking environments by using the OSI model as a guide.
Flow of Data in OSI Model
The OSI model depicts data communication as a seven-layered process. Data flows down from the top layers on the sending device to the bottom layer, where it’s transmitted physically. On the receiving device, the data travels up the layers in reverse order to be interpreted by the application.
Sending Device:
Step 1 – Application Layer (Layer 7): This is where the user interacts with the data, like composing an email.
Step 2 – Presentation Layer (Layer 6): The data is prepared for transmission, such as compressing an image file.
Step 3 – Session Layer (Layer 5): A session is established between the sender and receiver for communication.
Step 4 – Transport Layer (Layer 4): Data is segmented into manageable packets for efficient transfer. Protocols like TCP and UDP operate here.
Step 5 – Network Layer (Layer 3): Routing information (addresses) is added to the packets to determine the path across the network.
Step 6 – Data Link Layer (Layer 2): Packets are encapsulated with MAC addresses for identifying devices on the local network. Error detection mechanisms are also employed here.
Step 7 – Physical Layer (Layer 1): The data is converted into electrical or optical signals for transmission over the physical medium (cables, Wi-Fi).
Receiving Device:
The data follows the same layers in reverse order. At each layer, the corresponding functionalities are performed to reassemble and interpret the data for the application layer to utilize.
OSI vs TCP/IP Model
Below are some major differences between the OSI model and the TCP/IP Model:
- OSI came from ISO, while TCP came from DOD.
- OSI allows easy changes, but TCP/IP resists modifications.
- OSI acts as a generic communication gateway, while TCP protocols fuel internet development, facilitating host connections.
- The OSI model adopts a vertical structure, but TCP follows a horizontal layout.
- OSI standardizes hardware devices, whereas TCP enables connections among computers without device standardization.
Advantages of OSI Model
Here are the advantages of the OSI model:
- A versatile model for guiding the development of any network architecture
- Changes in one layer don’t impact others with stable interfaces as it is a layered model
- Distinct separation of services, interfaces, and protocols. Layer protocols are easily replaceable and tailored to network requirements
- Supports both connection-oriented and connectionless services, enhancing versatility in networking solutions
Disadvantages of OSI Model
Disadvantages of OSI Model:
- Session and presentation layers often have minimal functionality when practically implemented in network protocols
- Theoretical OSI model neglects technology availability, hindering its practical application
- OSI’s timing clashed with TCP/IP’s established presence, leading to initial corporate reluctance
- Initial OSI model implementation was challenging, slow, and expensive due to complexity
These are the advantages and disadvantage of OSI Model.
Frequently Asked Questions
Q1. What is the 7 layers of the OSI model?
The 7 layers of the OSI model are: Application Layer, Presentation Layer, Session Layer, Transport Layer, Network Layer, Data Link Layer, and Physical Layer.
Q2. What is the OSI model explained?
The OSI model is a conceptual framework that describes how different network components communicate. It consists of seven layers, each with a specific function and protocol. The OSI model helps to standardize and troubleshoot network systems.
Q3. What is OSI model format?
OSI model format is simply divided into 7 layers. Each layer has a different function and can communicate with one another.
Q4. What is the Fullform of OSI?
The full form of the OSI is Open System Interconnection. It works by dividing the OSI model into seven layers.
Conclusion
The OSI model is necessary to understand how data communication works within a network. In this blog, we have explained the OSI model and its seven types in detail, along with their functions and protocols.