Introduction
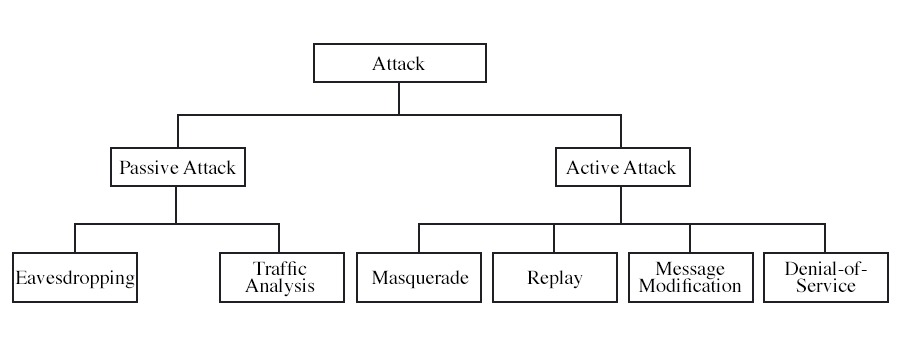
Clearly, the Internet is one of the most significant innovations of our time. It has simplified our life in more ways than we can even count. This development has similarly exposed us to a wide variety of cyberattacks. Cybersecurity attacks pose a greater threat to all that is part of the Internet. Cybersecurity threats are further classified into active attack and passive attack. But what exactly are these attacks?
This blog will mainly focus on cybersecurity attacks, their types, and the basic difference between active and passive attacks.
Before getting into more details, let’s first understand Cyber security attacks.
What is a Security Attack?
When someone takes illegal or unauthorized steps that put the security of a system at risk, it is known as a cyber security attack. These kinds of attacks aim to corrupt, delete, or steal private data or information. Mainly Cyber security attacks are of two types, i.e., active attack and passive attack. Join Ethical Hacking Course to learn more about cyber attacks and how to save your organization from these attacks.
Difference between Active and Passive Attacks
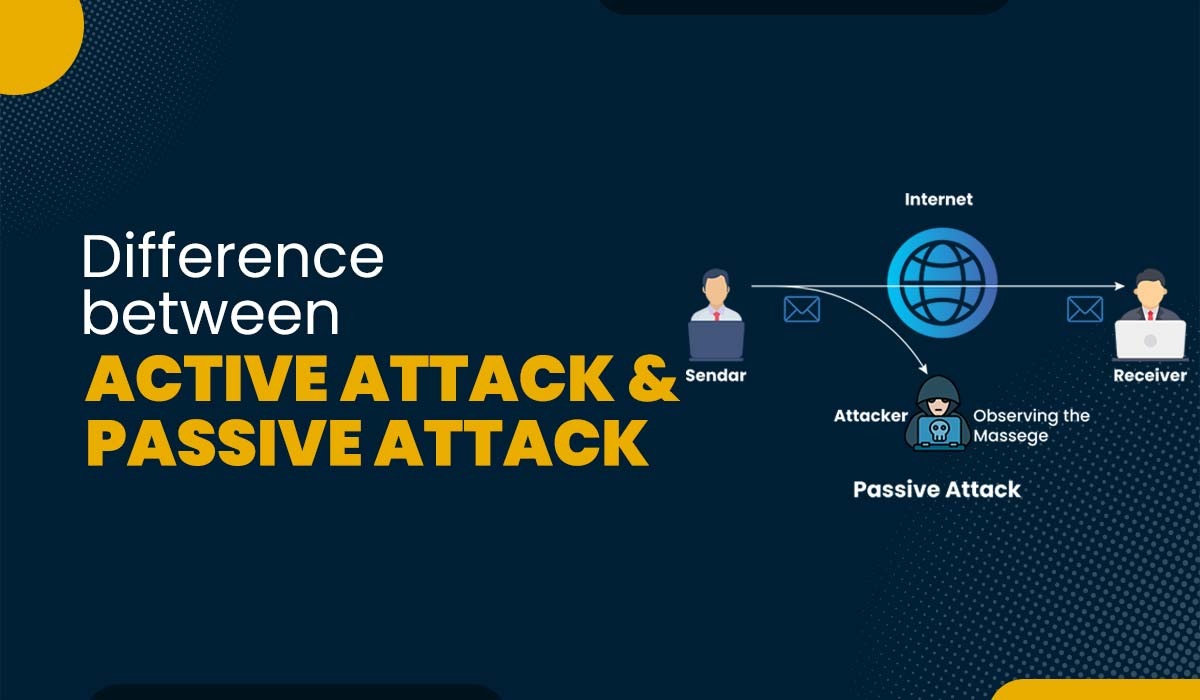
The main difference between active and passive attacks lies in the methodology: active attacks interact directly with the target system to modify or disrupt its functionality, passive attacks focuses on surveillance attacks and covert intelligence gathering that do not directly affect the target system. Here are some other differences:
| Parameters | Active Attacks | Passive Attacks |
|---|---|---|
| Initiation | Actively Initiated by the attacker. | Attacker passively observes and collects information. |
| Interaction | Involves direct interaction with the system or network. | No direct interaction. |
| Objective | To change or disrupt data or systems. | To collect or observe information. |
| Frequency | Mostly less frequent as it involves higher risk and visibility. | Can be frequent as it relies on stealth and might go undetected for a long period of time. |
| Impact | Data integrity, availability, or confidentiality may be compromised; system functionality or performance may be degraded or disrupted; unauthorized access or control may be gained. | Data confidentiality may be compromised; system behaviour or configuration may be revealed; network topology or activity may be mapped. |
| Detection | Easier to detect due to changes or anomalies in data or systems. | Harder to detect due to the lack of changes or anomalies in data or systems. |
| Visibility | Visible and leaves traces in logs and network traffic. | Less visible and often leaves minimal traces. |
| Prevention | It can be prevented or mitigated by using encryption, authentication, authorization, firewall, antivirus, etc. | It can be prevented or mitigated by using encryption, obfuscation, masking, tunneling, etc. |
| Response Time | Requires immediate response as attacker is actively affecting. | Response time may delayed as it doesn’t affect user in real-time. |
| Duration | The duration of the active attack is lower compared to the passive attack. | The duration of the passive attack is much longer as it is based on observing the data for as much time as possible. |
| Example | Denial-of-service, replay, masquerade, message modification | Eavesdropping and traffic analysis. |
| Common Techniques | Exploiting vulnerabilities, Sending malicious payloads, Brute-force attacks | Sniffing, Social Engineering, Passive reconnaissance |
Now, let’s discuss each attack type in detail to compare Active attacks vs Passive attacks.
What are Active Attacks?
In an active attack, the hacker deliberately attempts to alter the original message or data. These types of attacks pose a significant risk to the system’s integrity and availability. These assaults cause harm to systems and may even modify data. Due to the wide variety of physical and software weaknesses, protection against these assaults is challenging. The adverse effects caused by these attacks can have significant consequences on the system and its resources.

One positive aspect of this attack is that the victim is alerted when an active attack is being carried out. Rather than prioritizing prevention, the emphasis is placed on the detection of attacks and the subsequent restoration of the system. An active attack usually requires more effort and involves more challenging consequences.
Types of Active Attacks
Active attacks are classified into four types. These are:
- DOS attack: It stands for Denial-of-Service attacks. In this type of attack, the attacker floods the system with fake requests or data in order to make a service, website, or server unavailable. Here are the differences between DoS and DDoS Attacks.
- Masquerade: In this type of attack, the attacker disguises himself and pretends to be a legitimate user. With this, the attacker can easily steal sensitive information, which can cause many security issues for the user.
- Message Modification: In this type of attack, the attacker modifies or delays the original information or data for its own benefit. For example, if someone sends the message “This message is for Rahul” and is confidential, the attacker might update the message to “This message is for Kevin.” By this, the attacker will get access to confidential information, which is only for Rahul.
- Replay: A replay attack refers to the act of capturing and transmitting a message with the intention of generating an authorized result. With this attack, the attacker replicates the entirety of the data present within a network in order to utilize it for their own objectives in the future.
Defending against Active attacks
Here are a few measures to defend against active attacks:
- Install a firewall and intrusion detection/prevention systems.
- Use secure protocols like SSL/TLS and HTTPS.
- Install real-time monitoring tools to detect any threats to the system.
The following are a few preventive measures to take when facing such attacks:
- Using one-time passwords is a helpful step in ensuring the authenticity between individuals.
- Another effective measure is to generate a random session key, ensuring that it is unique and exclusive to a single transaction. This will prevent any attacker from sending the altered message once the session is over.
What are Passive Attacks?
In passive assaults, the attacker just monitors in on messages and steals any information they can get their hands on. They have dedicated themselves to monitoring every message and gathering information. The attacker does not attempt to change the content of the information he steals. These assaults pose a serious danger to the privacy of your information but can do no actual damage to the system.
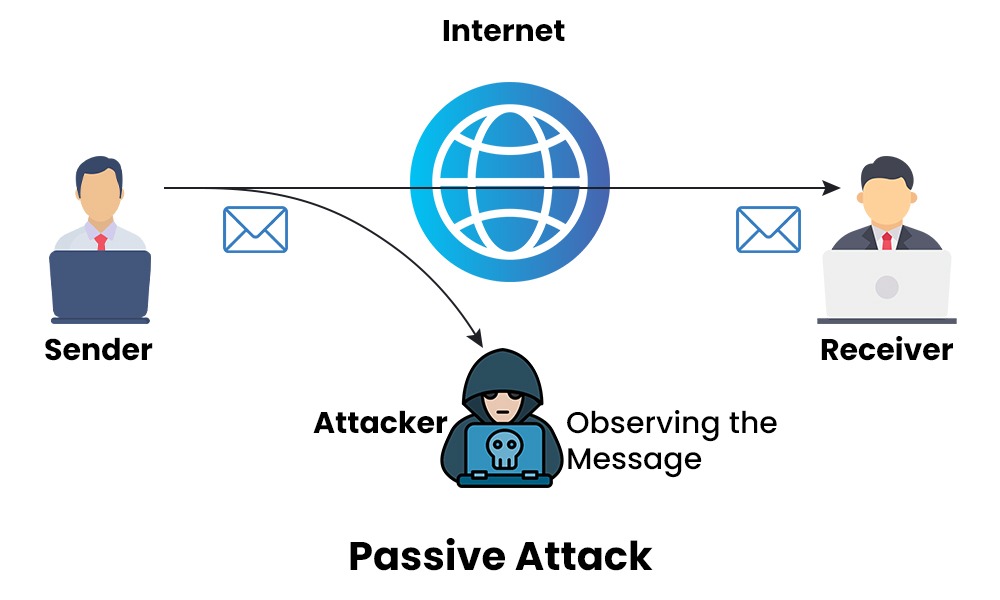
Since no data or information modification is involved, Passive attacks are harder to detect than Active ones. As a result, the attacked person has no idea they are being attacked. However, there are encryption methods that can be used to stop this. This makes the communication inaccessible to hackers at any stage of the transmission process. This is why it’s important to focus on prevention rather than detection.
Type of Passive Attacks
Passive attacks can easily take many forms, but it has been divided further into two. These are:
- Eavesdropping: In this type of attack, the attacker secretly listens to a conversation or communication that is not intended for him. It can be done for various purposes, such as gathering information, spying, or blackmailing.
- Traffic analysis: Traffic analysis is a passive attack that focuses on observing the exchange of information between two entities to extract valuable information. Even the encrypted data can be used by attackers to discover the geographical location and the identities of the communicating entities, along with details regarding the frequency and duration of the exchanged messages. This information is valuable in determining the nature of the ongoing communication.
Defending against Passive attacks
Here are some measures to be taken against passive attacks:
- You should encrypt all sensitive data with the latest encryption algorithms.
- Make sure your wireless systems are secure with strong passwords and WPA3.
- You should conduct regular security audits of your network to notice any passive attacks.
Below we have shown some of the preventive measures that one can take to prevent such attacks:
- If you don’t want attackers to get access to your network, don’t publish important information on social media.
- One can encrypt data in order to secure their personal information from attackers.
Now let’s compare Active attacks vs passive attacks.
Active Attacks vs Passive Attacks
The main difference between active and passive attacks lies in the methodology: active attacks interact directly with the target system to modify or disrupt its functionality, passive attacks focuses on surveillance attacks and covert intelligence gathering that do not directly affect the target system.
Other differences include:
Active attacks are usually aggressive as they look to modify a system’s data, disrupt its service, and compromise its integrity. Examples of active attacks include intermediary attacks, data manipulation, and denial attacks. On the other hand, passive attacks tend to be more insidious in nature, as their primary goal is nothing more than eavesdropping and stealing sensitive information without leaving much information. Examples include traffic analysis and intercepting unencrypted data.
Active attacks are easier to detect because they cause noticeable changes in the system, while passive attacks are harder to detect because they cause no changes in the system. Although both attacks pose a high risk, but passive attacks are generally considered more difficult to tackle.
Influence
Active Attacks: Their effects are immediate and disruptive.
Passive attacks: Results last longer and leak issues.
Mitigation
Active attacks: Firewalls, IDS and IPS.
Passive attacks: Secure encryption and communication techniques.
These are the difference between Active and Passive Attacks.
Frequently Asked Questions
Q1. What are the two basic types of attacks?
Mainly cyber security attacks are classified into two categories. These are – Active Attack and Passive Attack.
Q2. What are the basic difference between passive and active attacks?
The basic difference is in their mode of operation. When we talk about an active attack, the attacker updates or changes the data or information meant for the client. In the case of a passive attack, the attacker observes the information for a period of time to see the client’s behaviour and also stores that information for the future.
Q3. What is an active attack?
An active attack is a type of cyberattack that involves modifying, deleting, or injecting data into a network or system.
Q4. What are the various active attacks?
Active attacks are carried out in different forms. Some of which are:
- DOS attack
- Masquerade
- Message modification
- Replay
Conclusion
We have covered detailed information about cyber security attacks, i.e., active attack and passive attack. So, the main difference between active attack and passive attack is that Active attacks involve direct actions by an unauthorized entity to compromise a system, while passive attacks are attempts to gain unauthorized access or information without directly affecting the system’s operation. We can confidently conclude that such attacks bring significant risks to any company and can result in significant damage. It is critical to take some preventive measures to protect from such attacks.
Feel free to leave a comment below if you have any questions or concerns about this topic.