Introduction
If someone is preparing for a network-related job interview, it is possible that they may encounter some questions based on the OSI model. In order to help students clear their interviews, we have hand-picked some of the most asked and important OSI model Interview questions and answers for freshers as well as working professionals. These questions cover the most common and important topics related to the OSI model and provide detailed explanations for each answer.
About OSI Model
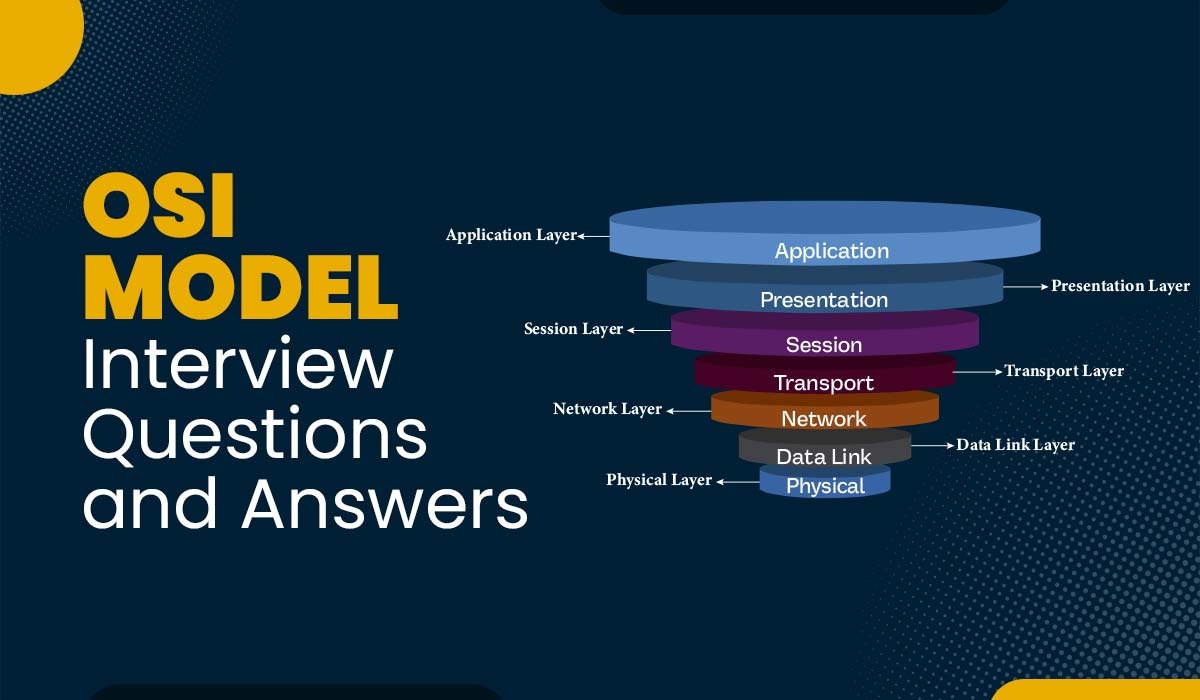
The OSI model is a conceptual framework that mainly describes how different protocols interact and communicate with each other. There are seven layers in the OSI model, each having a specific function. With the help of the OSI model, it is possible for network engineers as well as developers to design, troubleshoot, and maintain network systems.
Let’s begin with the basic OSI interview questions and answers.
Basic OSI Model Interview Questions and Answers
Here are some of the most asked basic OSI Model Interview Questions and Answers perfect for freshers.
Q1. What is the OSI model and what are its benefits?
The OSI or Open Systems Interconnection model is a fundamental reference model that defines how different network protocols communicate. It divides the network communication process into seven layers. These are physical, data link, network, transport, session, presentation, and application.
The benefits of the OSI model are:
- It assists in simplifying the network design and development process.
- It allows troubleshooting and debugging of network problems.
- It allows changes at one layer without affecting the other layers, offering modularity and flexibility.
Q2. What are the seven layers of the OSI model and explain their basic functions?
The seven layers of the OSI model are:
- Physical layer: It is responsible for transmitting as well as receiving raw bits over a physical medium. The physical medium can be cables, wires, or wireless signals.
- Data link layer: This is the second layer of the OSI model. It is mainly responsible for framing, addressing, error detection, and error correction of data packets.
- Network layer: It is responsible for functions like routing, forwarding, addressing, and congestion control of data packets. Apart from this, it also defines the logical structure as well as the topology of the network.
- Transport layer: This is the fourth layer of the OSI model. It is responsible for ensuring reliable, ordered, and error-free delivery of packets between end-to-end applications. There are other functionalities, such as assisting in defining the connection-oriented or connectionless services and protocols for data transmission.
- Session layer: It is responsible for establishing, maintaining, and terminating sessions between applications. Apart from this, it also defines the synchronization, authentication, authorization, and encryption mechanisms for data exchange.
- Presentation layer: This is the sixth layer of the OSI model. It is responsible for translating, formatting, compressing, and encrypting data between different formats and representations. The presentation layer also defines syntax and semantics.
- Application layer: This is the seventh and highest layer of the OSI model, which offers various services and protocols for specific applications on a network.
Q3. What are the different protocols used in each layer of the OSI model?
Different protocols used in each layer of the OSI model are:
| OSI Model Layers | Protocols |
|---|---|
| Physical layer | ADSL, ISDN, Bluetooth, Ethernet |
| Data link layer | ARP, MAC, HDLC, STP |
| Network layer | IP, ICMP, IGMP, RIP, BGP |
| Transport layer | TCP, UDP, GRE |
| Session layer | NFS |
| Presentation layer | SSL |
| Application layer | SSH, DNS, DHCP, NTP, HTTP |
Q4. What is the difference between TCP and UDP protocol?
The basic difference between the two protocols i.e., TCP and UDP is:
| Factors | TCP | UDP |
|---|---|---|
| Connection Type | Connection-oriented, meaning it establishes a connection before data transfer | Connectionless, meaning it does not establish a connection before data transfer |
| Data Sequence | Maintains the order of data packets by assigning sequence numbers to them | Does not maintain the order of data packets |
| Delivery | Guarantees the delivery of data packets by using acknowledgment and retransmission mechanisms | Does not guarantee the delivery of data packets |
| Check for Errors | Performs error checking by using checksums and windowing techniques | Performs minimal error checking by using checksums only |
| Broadcasting | Does not support broadcasting or multicasting | Supports broadcasting and multicasting |
| Data Retransmission | Retransmits the lost or corrupted data packets until they are received correctly | Do not retransmit the lost or corrupted data packets |
| Speed | Slower than UDP due to more overhead and complexity | Faster than TCP due to less overhead and simplicity |
Q5. What are some examples of devices that operate at different layers of the OSI model?
Some devices that operate at different layers of the OSI model are:
| OSI Model Layer | Devices |
|---|---|
| Physical layer | Hub, repeater |
| Data link layer | Switch, bridge, Network Interface Card |
| Network layer | Router |
| Transport layer | Gateway, firewall |
| Session layer | Proxy server |
| Presentation layer | Encryption device |
| Application layer | Web server, phones |
Q6. Is there any alternative model to the OSI model?
Yes, one possible alternative to the OSI model is the TCP/IP model. It is a concise version of the OSI model that consists of four layers instead of seven. The TCP/IP model is also known as the Internet model, as it describes how the Internet works. The four layers of the TCP/IP model are:
- Application Layer
- Transport Layer
- Internet Layer
- Network Layer
Q7. What are some common network problems that can occur at different layers of the OSI model?
Some of the network problems that can occur at different layers of the OSI model are:
| OSI Model Layer | Network Problems |
|---|---|
| Physical layer | Damaged cables, loose connectors, interference, signal attenuation |
| Data link layer | Frame errors, collisions, MAC address conflicts |
| Network layer | IP address conflicts, routing loops, packet loss |
| Transport layer | Port conflicts, connection timeouts, segment reordering |
| Session layer | Session hijacking, session termination |
| Presentation layer | Data corruption, encryption errors |
| Application layer | Protocol mismatch, service unavailability |
Q8. What is encapsulation and decapsulation in the context of the OSI model?
Encapsulation is the process of adding headers and trailers to data at each layer of the OSI model as it travels down from the application layer to the physical layer. Each header contains information relevant to that particular layer’s function (such as source and destination addresses, sequence numbers, checksums, etc.). Each trailer contains information for error detection and correction (such as CRC). Encapsulation allows each layer to perform its function without worrying about the details of the other layers.
Decapsulation is the reverse process of encapsulation, which involves removing headers and trailers from data at each layer of the OSI model as it travels up from the physical layer to the application layer. Each layer reads and processes the information in the header and trailer, then passes the data to the next higher layer. Decapsulation allows each layer to retrieve the original data sent by the source application.
Q9. What is the difference between an IP address and a MAC address?
The basic difference between an IP address and a MAC address is:
| Factors | IP Address | MAC Address |
|---|---|---|
| Full Form | Internet Protocol Address | Media Access Control Address |
| Number of Bytes | 4 bytes for IPv4, 16 bytes for IPv6 | 6 bytes |
| Format | IPv4: 192.168.1.1 IPv6: fe80::c504:e3c2:c49d:543b%5 | 00-B0-D0-63-C2-26 |
| Protocol used for retrieval | Reverse Address Resolution Protocol (RARP) | Address Resolution Protocol (ARP) |
| Provider | Internet Service Provider (ISP) or network administrator | Network Interface Card (NIC) manufacturer |
| Operation | Operates on the network layer of the OSI model | Operates on the data link layer of the OSI model |
Q10. What is a port number?
A port number is a logical address assigned to each application or process that uses a network or the Internet to communicate. It uniquely identifies a network-based application on a computer. Each application or program is allocated a 16-bit integer port number. This number can be assigned automatically by the operating system, manually by the user, or set as a default for some popular applications.
Below are some examples of the protocols along with the port number.
| Port Number | Protocols |
|---|---|
| 20, 21 | File Transfer Protocol (FTP) |
| 22 | Secure Shell (SSH) |
| 23 | Telnet Protocol |
| 25 | Simple Mail Transfer Protocol (SMTP) |
| 53 | Domain Name System (DNS) |
| 67, 68 | Dynamic Host Configuration Protocol (DHCP) |
| 80 | HyperText Transfer Protocol |
| 110 | Post Office Protocol (POP3) |
| 137 | NetBIOS Name Service |
| 143 | Internet Message Access Protocol (IMAP4) |
| 443 | Secure HTTP (HTTPS) |
These are some of the most important OSI Model Interview Questions. Let’s now begin with the advanced OSI interview questions and answers.
Advanced OSI Model Interview Questions and Answers
Here are some of the most important OSI Model Interview Questions and Answers for Working Professionals.
Q11. What is port forwarding, and why do network administrators use it?
Port forwarding, also known as port mapping, is a technique used in networking to allow external devices to communicate with devices on a local network. It works by forwarding incoming traffic from a specific port on a router to a particular port on a device within the local network. This enables devices within the local network to be accessible from outside the network.
Network Administrators use it for many purposes. Some of these are:
- Remote access: Suppose you’re at the office and want to connect to your home computer. By port forwarding SSH (port 22) in your router to your computer’s IP address, anyone trying to SSH to your public IP address will be forwarded to your home computer.
- Hosting services: If you want to host a website or run a Minecraft server on your computer, port forwarding HTTP (port 80) or HTTPS (port 443) allows others on the internet to access these services hosted on your machine.
Q12. How does a router function at the Network layer?
A router functions at the Network layer of the OSI model. Its primary role is to manage traffic between different networks by forwarding data packets to their intended IP addresses. Apart from this, routers allow multiple devices to use the same Internet connection. Some of the functions of the router are:
- Routing: A router determines the best path for data transmission from the source to its destination. It doesn’t just transmit packets; it selects the optimal route.
- Logical Address Assignment: The network layer assigns logical addresses (such as IP addresses) to devices sending or receiving data packets. These addresses uniquely identify devices within a network. Logical addressing ensures data integrity by confirming that packets are sent by authorized senders and received by the intended recipients.
- Host-to-Host Delivery (Forwarding): This process involves transmitting or forwarding data packets via routers along the determined path.
Q13. What is Unicasting, Multicasting, and Broadcasting in a network?
Unicast – Unicast is a communication method where a message is sent from one sender to one receiver. It’s essentially a one-to-one transmission.
For example, if a device with IP address ‘10.1.2.0’ wants to send data packets to a device with IP address ‘20.12.4.2’ in another network, unicast comes into play.
Broadcast – Broadcasting involves transmitting data from one or more senders to all receivers within the same network or across other networks.
It’s useful for network management packets such as ARP (Address Resolution Protocol) and RIP (Routing Information Protocol), where all devices must receive the data.
Multicast – Multicast involves transmitting data from a single source host to a specific group of hosts interested in receiving that data. It lies between unicast (one-to-one) and broadcast (one-to-all) methods. You can also find the differences between Broadcast and Multicast.
Q14. What is “segmentation” in the context of the Transport layer?
Segmentation in the context of the Transport layer refers to the process of dividing a data packet into smaller units for transmission over a network. This happens at layer four of the OSI model, which is the transport layer.
When data arrives at the transport layer from the upper layers, it is divided into segments. These segments are smaller units that allow efficient network transmission. Each segment contains a sequence number, enabling the transport layer to reassemble the message at its destination correctly. If any packets are lost during transmission, this process identifies and replaces them.
Q15. How can you use the ping command for troubleshooting?
When you “ping” something on a network, you send an internet packet (specifically, an ICMP echo request) to a destination computer or network device. The target device responds by sending a packet back to you. Most commonly, we want to know how long the reply takes, expressed in milliseconds (lower numbers are better).
Now, how to use the ping?
On Windows:
- Open the Start Menu, search for “Command Prompt,” and select it.
- Type ‘ping’ followed by either:
- The IP address of the device (e.g., ‘ping 8.8.8.8’).
- The URL of a site (e.g., ‘ping google.com’).
- Ping will send four packets of data.
- If any packets show “request timed out,” your computer didn’t receive a reply from the target.
Q16. What is the difference between flow control and error control?
The basic difference between the flow control and error control is:
| Factors | Flow Control | Error Control |
|---|---|---|
| Purpose | Ensures proper transmission of data from sender to receiver | Delivers error-free and reliable data to the receiver |
| Approaches | Feedback-based Flow Control Rate-based Flow Control | Detecting errors: Parity checking, Cyclic Redundancy Code (CRC), and checksum |
| Impact | Prevents overrunning of receiver buffers and data loss | Detects and corrects errors in transmitted data frames |
| Impact | sliding window protocol, stop-and-wait protocol | Stop & Wait ARQ – Sliding Window ARQ (Go-back-N ARQ, Selected Repeat ARQ) |
Q17. What is the role of the firewall in the OSI model’s context?
In the context of the OSI model, a firewall plays a crucial role in securing computer networks. Let’s understand the functions of firewalls and how they operate within the layers of the OSI model.
- Network Layer (Layer 3)
Firewalls primarily work as static packet filtering at the network layer. These firewalls are responsible for examining individual data packets which are based on the packet’s source and destination address.
- Transport Layer (Layer 4)
Apart from the functioning of firewalls at the network layer, it also functions at the transport layer. At this layer, firewalls inspect TCP and UDP traffic.
- Application Layer (Layer 7)
Most of the firewall functions at the lower layers of the OSI model. There are some advanced ones that can understand the application layer. At this layer, they usually deal with specific applications as well as protocols.
Q18. What is CRC and at which layer does CRC work?
CRC stands for Cyclic Redundancy Check, an error-detecting code commonly used in digital networks and storage devices to detect accidental changes to digital data.
CRCs are good at detecting common errors that are mainly caused by noise in transmission channels. The check value generated by CRCs has a fixed length and is occasionally used as a hash function.
CRC operates at the Data link layer of the OSI model.
Q19. What is the difference between half-duplex and full-duplex?
The difference between the two i.e., half-duplex and full duplex is:
| Factors | Half-duplex | Full-duplex |
|---|---|---|
| Data Flow | Two-directional, but one at a time | Two-directional and simultaneous |
| Channel Usage | Utilizes one channel for data transmission | Uses two channels due to splitting for simultaneous sending and receiving |
| Performance | Provides less performance than full-duplex mode | Offers better performance than half-duplex mode |
| Bandwidth Utilization | Less utilization of bandwidth during transmission | Doubles bandwidth utilization |
| Communication channel | Saves bandwidth by alternating between both sides on a single channel | Utilizes the entire capacity by splitting the channel for simultaneous bidirectional transmission |
Q20. Which layer provides the logical addressing that routers will use for path determination?
The network layer provides the logical addressing in the form of IP addresses. The routers use this for path determination. This layer is mainly responsible for routing data packets from the source to the destination based on these logical addresses. With the use of IP addresses and routing, routers can determine the best path to transmit the data.
These are the top 10 most asked OSI Model Interview Questions for advanced professional roles.
Conclusion
Mastering the OSI Model is crucial for anyone who is preparing for the interview for the job role in networking. By understanding its layers and their functions, you will be well-prepared for the interview. In this blog, we have hand-picked 20 OSI model Interview questions for both beginners and professionals that will assist in clearing the interview with ease.
Remember to review additional questions related to the OSI Model to enhance your knowledge further! If you have any suggestions or queries, feel free to use the comment section below.