Introduction
The transport layer is one of the seven layers of the OSI model, which is a reference framework that explains the process of transmitting data between computers. The OSI model was developed by ISO in 1984 and is now considered as an architectural model for inter-computer communications. Transport layer protocols play a significant role in defining how the transport layer performs its function. In this blog, we will explain the transport layer with its responsibilities and protocols used in transport layer in detail.
Transport Layer Protocols are an essential part of networking as they provide a way to transmit data packets from one node to another. So, if you are learning CCNA or preparing to move ahead in your career with ENCOR 350-401 Training or other, you need to have a deep understanding of these protocols. Before moving to the transport layer protocols, let’s first understand the basic knowledge about the transport layer.
What is Transport Layer?
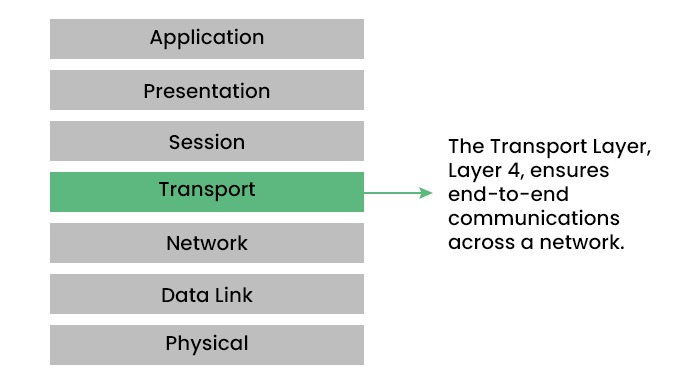
The transport layer is the fourth layer in the OSI model that provides end-to-end delivery of data as well as reliable and efficient communication between two or more devices running on different hosts. It is responsible for ensuring the data that is delivered must be in the same order and without any error or loss.
It operates above the network layer, which handles the routing of packets across different networks, and below the session layer, which manages the establishment and termination of connections. Below, we have shown the position of the transport layer in the OSI model.
Responsibilities of Transport Layer
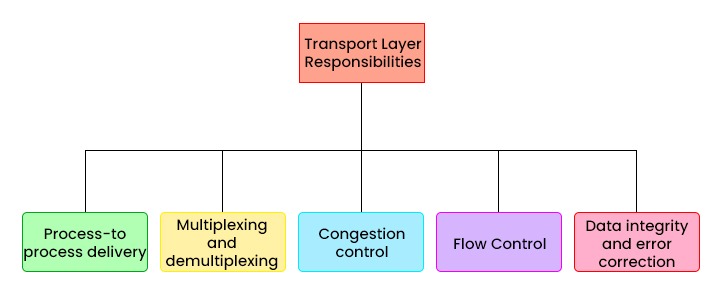
The transport layer carries out various responsibilities. Some of these are process-to-process delivery, multiplexing and demultiplexing, flow control, congestion control, data integrity, and error correction. Below, we have discussed each responsibility in detail.
Process-to-process delivery
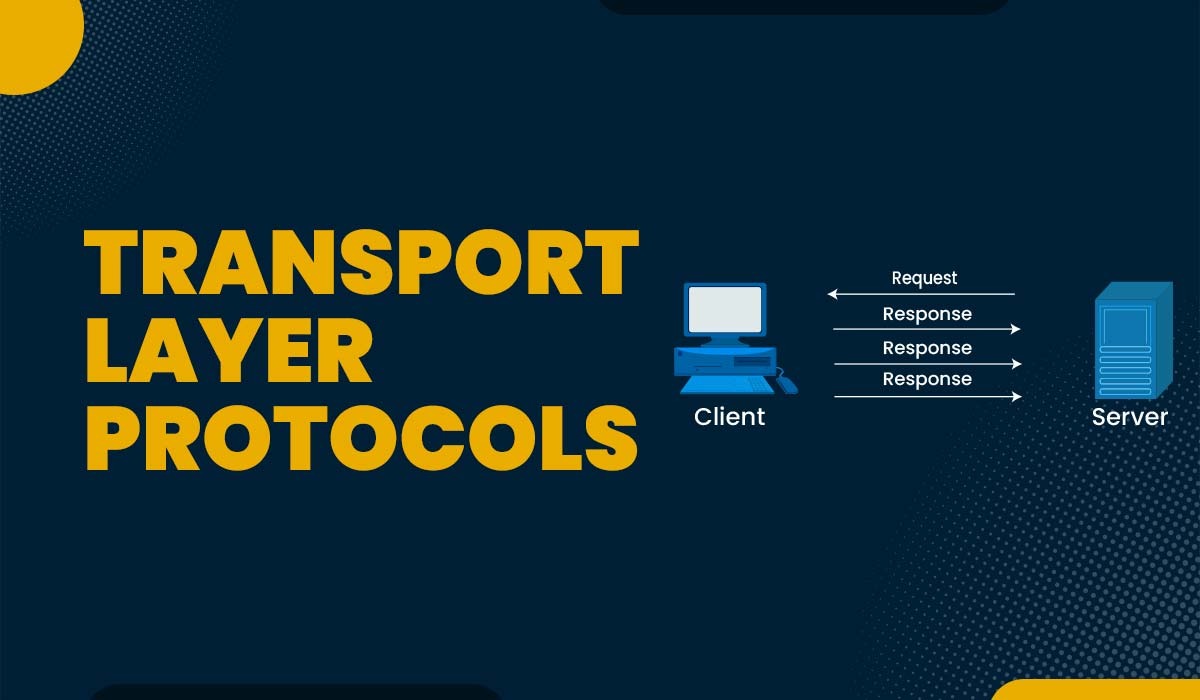
It is the job of the transport layer to guarantee that data is transferred from one process to another independent of network layer protocols. It employs port numbers to distinguish between the source and destination processes. Port numbers are logical identifiers that help differentiate various programs on the same host. For example, port 80 is commonly used for web servers, port 25 for email servers, and so on.
Multiplexing and demultiplexing
The transport layer can multiplex multiple application data streams into one transport layer data stream and demultiplex them at the destination. This allows multiple applications to share the same network resources.
Flow control
In order to regulate the amount of data that can be sent by the sender and received by the receiver and considering their buffer space and processing capacity, the transport layer implements flow control techniques such as sliding windows or stop and wait.
Congestion control
The transport layer continually checks network conditions in order to alter data transmission rates to avoid overwhelming network resources and congestion. It utilizes algorithms such as start, congestion avoidance, quick retransmit, and fast recovery for congestion control.
Data integrity and error correction
To guarantee that transmitted data stays uncorrupted or unmodified throughout transmission, the transport layer employs error detection methods such as checksums or cyclic redundancy checks (CRC). It may also repair problems using techniques like retransmission, acknowledgment, and timeout mechanisms.
Now that we have a basic understanding of the transport layer, let’s discuss the protocols used in transport layer in detail.
What are Transport Layer Protocols?
Transport layer protocols are the rules and standards that define how the transport layer functions and interacts with other layers. They operate at Layer 4 of the OSI model and act as intermediaries between applications running on different devices and the underlying network layer. Their main job is to ensure reliable and efficient data exchange between applications.
Understanding Transport Layer Protocols is crucial for anyone who wants to grasp how applications communicate over networks. They ensure smooth, efficient, and reliable data exchange, forming the backbone of internet communication.
Mainly, there are three types of transport layer protocols. These are:
- UDP (User Datagram Protocol)
- TCP (Transmission Control Protocol)
- SCTP (Stream Control Transmission Protocol)
Characteristic of Transport Layer Protocols
Below are the characteristics of Transport Later Protocols:
- A process is a program that is running; an operating system can support situations with numerous users and processes.
- The transport layer consists of two protocols: TCP and UDP.
- At the network layer, the IP protocol transfers a datagram from a source host to a destination host.
- Each port is defined by a positive integer address made up of 16 bits.
- When a host delivers a message to another host, that host’s process is transmitted to a destination process by the source process. The protocols of the transport layer define connections to specific ports, also called protocol ports.
Let’s now discuss the three Transport Layer Protocols.
UDP (User Datagram Protocol)
UDP is a connectionless and unreliable protocol that offers fast and simple transferring of data. UDP does not guarantee the delivery of data. Apart from this, UDP does not carry out various other functions such as flow control, congestion control, or error correction mechanisms. When we talk about UDP, it is primarily suitable for applications that require low latency, high throughput, or real-time communication. Some of the applications of UDP are voice-over IP (VoIP), video streaming, and online gaming.
Now, the question that arises is how data transfer occurs in the UDP case. Below, we have discussed in simple steps.
- UDP utilizes datagrams as the units in order to transfer data. Each datagram comprises a header and a payload. The header contains information such as the source port number, destination port number, datagram length, and a checksum.
- UDP transmits datagrams to the network layer without verifying if the destination is available or ready to receive data.
- In contrast to other protocols, UDP does not maintain a record of the sequence or order in which datagrams are received. This means that datagrams may arrive at the destination out of order, duplicated, or even get lost.
- Furthermore, UDP does not provide any acknowledgment or retransmission mechanism for the datagrams that have been sent. It is solely the responsibility of the application layer to handle any errors or losses that occur during transmission.
UDP Header Format
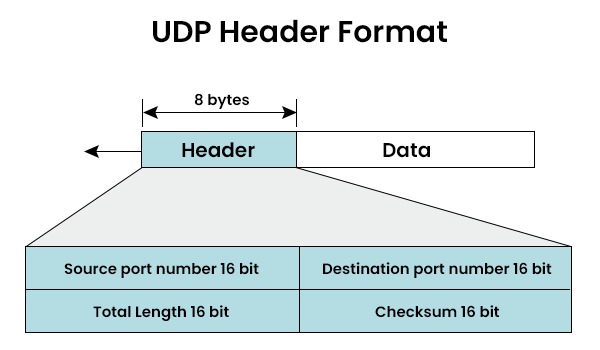
The UDP header consist of four components:
- Source Port Number – The port on which the packet will be sent is identified by Source port number which is 16 bits of information.
- Destination Port Number – It indicates which port will receive the data. The destination machine’s application-level service is identified using Destination port number (16-bit information).
- Length – The length of the UDP packet, including the header, is specified by this 16-bit field. Since the header consists of 8 bytes, the minimum value would be 8 bytes.
- Checksum – This is an optional field with 16 bits. Due to the possibility of data corruption during transmission, this checksum field verifies the accuracy of the data.
Notes: Unlike TCP, UDP does not require checksum calculation. UDP does not offer flow control or error control. Therefore, IP and ICMP are necessary for UDP to notify errors. In addition, UDP offers port numbers for distinguishing between user requests.
Advantages of UDP
Here are the some of the advantages of UDP –
- Data transfer via multicast and broadcast is also possible with UDP
- UDP protocol is often used for quick operations like DNS lookups
- Since it is a connectionless protocol, having a connection-oriented network is not required
- Message transport using UDP is quick
Disadvantages of UDP
Here are the some of the disadvantages of UDP –
- The delivery of a packet is not guaranteed while using the UDP protocol
- Packet loss is worse for UDP protocol
- There is no congestion control mechanism in the UDP protocol
- The data cannot be transmitted sequentially over the UDP protocol
Let’s move on to the next protocol in Transport Layer Protocols.
TCP (Transmission Control Protocol)
TCP is a connection-oriented and reliable protocol that offers a secure transfer of data in an orderly manner. TCP guarantees the delivery of data by establishing a connection. Apart from this, TCP offers flow control, congestion control, and error detection mechanisms. It is suitable for applications that require reliability, accuracy, or integrity of data. Examples of TCP include web browsing, email, file transfer, or remote access.
Now, the question that arises is how TCP operates. Below, we have explained the TCP’s functioning in detail.
- In order to transfer data from the source to the destination, TCP utilizes segments as the unit of data. A segment consists of a header and a payload. The header contains information such as the source port number, the destination port number, a sequence number, an acknowledgment number, a window size, some flags, and a checksum. Below, we have shared an image to show the TCP data format.
- In order to establish a connection, TCP initiates a three-way handshake between the source and the destination. The source sends a segment with the SYN flag set in order to request a connection. The destination then responds with a segment with the SYN and ACK flags set to acknowledge the request. After this, the source sends another segment with the ACK flag set to confirm the connection.
TCP Header Format
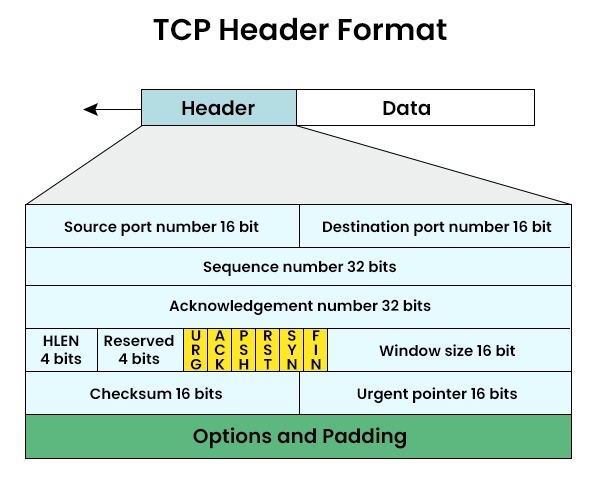
Here are the components of TCP header –
- Source port address – A 16-bit parameter called the source port address indicates the port number of the application software providing the segment.
- Destination port address – A 16-bit parameter called the destination port address indicates the port number of the application program receiving the segment.
- Sequence number – The number allocated to the first byte of data in a segment is defined by the sequence number, a 32-bit field.
- Acknowledgement number – An acknowledgement number is a 32-bit field that indicates the byte that the recipient anticipates hearing from the sender next.
- Header Length (HLEN) – The number of 4-byte words in the TCP header is indicated by the 4-bit field called Header Length (HLEN). The TCP header length can range from 20 to 60 bytes.
- Reserved – It is a field 6 bit that is set aside for a future purpose.
- Flags – In this field, there are six distinct independent control bits.
- URG: Urgent pointer
- ACK: Acknowledgement number
- PSH: Push request
- RST: Reset connection
- SYN: Sequence number Synchronization
- FIN: Connection termination
- Window Size – The size of the TCP transmission window is specified in bytes by this 16-bit field.
- Checksum – Error detection uses this 16-bit field, which has a checksum.
- Urgent pointer – The urgent data in the data segment triggers the setting of this flag.
- Options – This field in the TCP header can hold up to 40 bytes of optional data.
Advantages of TCP
Here are the some of the advantages of TCP –
- Data delivery and a connection-oriented protocol are offered by TCP
- Multiple routing protocols are supported by TCP
- Error control and flow control are characteristics offered by TCP protocol
- The TCP protocol functions separately from the operating system’s protocol
Disadvantages of TCP
Here are the some of the disadvantages of TCP –
- It is challenging to replace a protocol in TCP/IP
- Transmission via broadcast or multicast is not possible with TCP protocol
- The TCP protocol does not provide a distinct division between its interface, services, and protocols
- Block boundaries do not exist in TCP protocol
Let’s discuss the third type in the list of transport layer protocols, i.e., SCTP.
SCTP (Stream Control Transmission Protocol)
SCTP is a connection-oriented protocol. With the help of SCTP, data is sent in full duplex mode from sender to recipient. It is unicast in nature, allows point-to-point connections, and employs many hosts to reach the target. It makes it easier to establish a connection across a wireless network.
The SCTP protocol ensures dependable data delivery. SCTP offers a reliable and simpler phone call via the Internet. The multihoming feature of the SCTP protocol is supported; that is, it is independent of the IP layer and may create many connection paths between the two communication locations. By prohibiting half-open connections, the SCTP protocol further improves security.
Advantages of SCTP
Here are the some of the advantages of SCTP –
- The secure protocol is SCTP
- A connection in full duplex is offered by SCTP. Data can be sent and received simultaneously by it
- The IP layer is independent of the SCTP protocol
- The TCP and UDP protocols’ characteristics are both present in the SCTP protocol
Disadvantages of SCTP
Here are the some of the disadvantages of SCTP –
- Applications must be modified if SCTP is utilized in place of TCP or UDP protocol
- For the SCTP protocol, the node’s transport stack needs to be modified
- The apps must be adjusted appropriately in order to handle many streams concurrently
These are the three Transport Layer Protocols.
Frequently Asked Questions
Q1. What are the transport layer protocols?
Transport layer protocols are rules and regulations mainly used to assist the transport layer in interacting with other layers of the OSI model. Mainly, there are 3 types of transport layer protocols, namely UDP, TCP, and SCTP.
Q2. What are the transport layer 4 protocols?
The transport layer, i.e. layer 4 protocols, defines the rules and standards for the transport layer functions and interactions with other layers.
Q3. What are the two main transport protocols?
The two main transport layer protocols are TCP and UDP. TCP stands for Transmission Control Protocol, and UDP stands for User Datagram Protocol.
Q4. What is TCP and UDP?
TCP and UDP are protocols for data transmission. TCP ensures reliable and ordered delivery, but is slower. UDP is faster, but does not guarantee delivery or order.
Conclusion
In this blog, we have discussed what the transport layer is, the different responsibilities, and different types of transport layer protocols. We have learned that UDP, TCP, and SCTP are the three main types of transport layer protocols, all having different functions and performances.
Feel free to comment below if you have any suggestions or doubts regarding the topic. For any Networking Training, checkout our courses.