Introduction
In networking, as we know, switches are used to create networks, while routers are used to connect different networks. By default, switches forward both broadcast and multicast out of every port but not the originating one. However, if you require to divide a single broadcast domain into smaller ones with security in some networks, then it is possible with the VLAN concept. In this blog, we will understand what is VLAN and everything else you need to know about it.
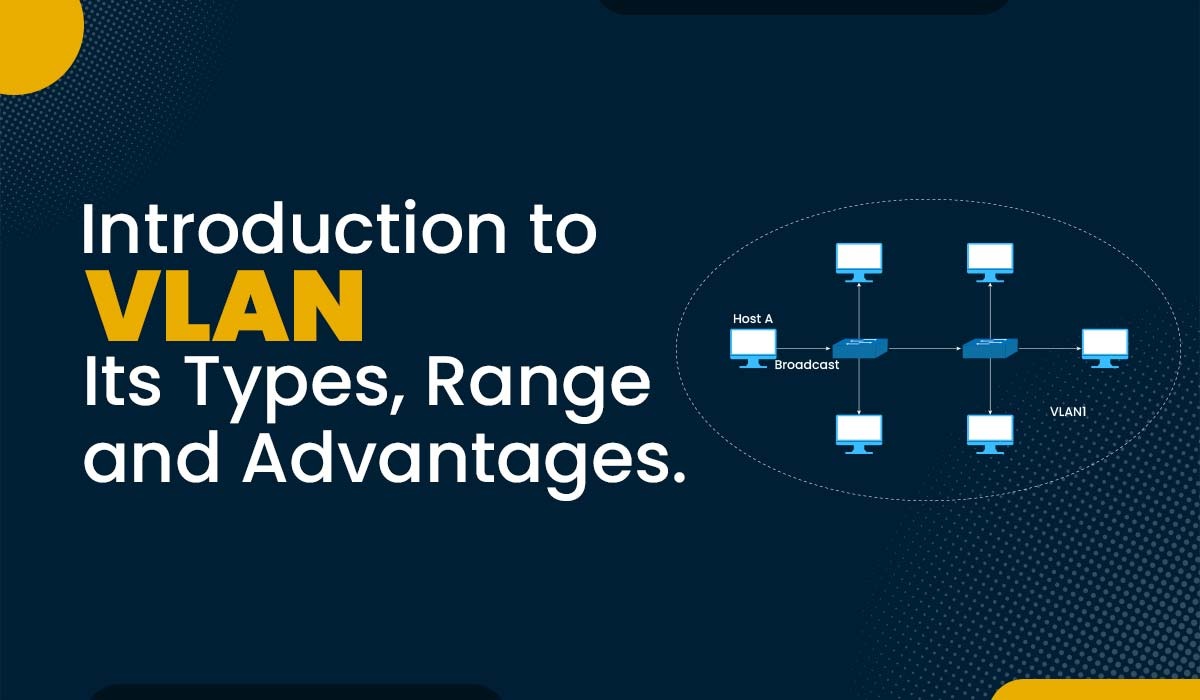
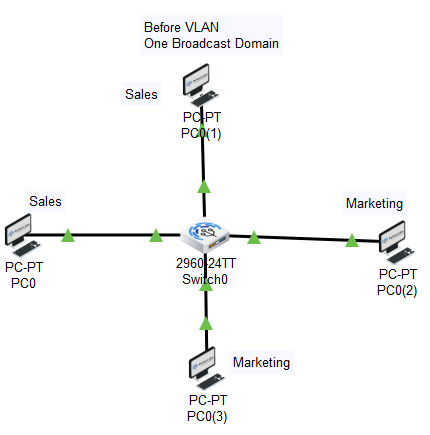
A broadcast sent from a host can easily reach all network devices in the absence of VLANs. Every device will process received broadcast frames. It can potentially increase CPU overhead on each device while decreasing overall network security.
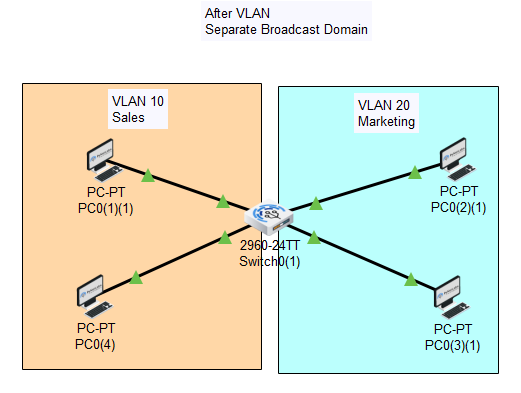
In case you place some interfaces on switches into separate VLANs, a broadcast from one host can reach only devices available inside the same VLAN. Hosts of VLANs will not even be aware that the communication took place, and all departments or groups work separately with their broadcast domain.
What is VLAN (Virtual Local Area Network)?
VLAN or Virtual Local Area Networks are nothing but a logical grouping of switch ports to have separate broadcast domains. VLAN reduces the size of broadcast domains while increasing the number of broadcast domains.
VLANs are typically configured on switches by assigning some interfaces to one broadcast domain and others to another. Each VLAN serves as a subset of the switch ports on an Ethernet LAN.
VLANs can be configured on multiple switches, with each VLAN being treated as its own subnet or broadcast domain. The broadcasted frames onto the network will only be switched between the same VLAN ports.
- VLANs in networking are identified by a unique number called VLAN ID.
- A Valid ID range is 1-4094. On a VLAN switch, you assign ports with the proper VLAN ID.
- The switch then allows data that must be sent between various ports with the same VLAN ID.
Before VLAN working of a switch
After VLAN working of a switch
Let’s take a deep dive into VLAN, starting with how it works.
How VLAN works?
Here are step-by-step instructions on how VLAN works:
- In networking, VLANs are designated by a number.
- The range is 1 to 4094. You assign ports on a VLAN switch with the correct VLAN number.
- The switch then permits data to be transmitted between different ports belonging to the same VLAN.
- There should be a means to transport traffic between switches because practically all networks are bigger than a single switch.
- Assigning a port on each network switch with a VLAN and connecting a cable between them is one quick and straightforward approach to accomplish this.
Purpose of Virtual Local Area Network
The purpose of VLAN in networking is as follows –
- Improve performance
By limiting the amount of traffic a specific endpoint sees and processes, VLANs can enhance performance for devices on them. By dividing broadcast domains, VLANs limit the number of other hosts that a given device can see broadcasts from. For example, phones won’t receive any broadcast traffic created by workstations if they are all on one VLAN but all workstations are on another. Each can limit the traffic on their respective networks that is relevant.
Different Traffic handling rules per VLAN can be defined by the Network Engineers. For example: To help ensure the functionality of telepresence devices, they can implement rules to prioritise video traffic on a VLAN that connects conference room equipment.
2. Enhanced security
By allowing for greater control over which devices have access to one another, VLAN partitioning can also enhance security. for example, Network teams might limit management access to network hardware or IoT devices to particular VLANs.
3. Smooth administration
Administrators can also organize devices for purely administrative, non-technical reasons by using VLANs to group endpoints. For example, they might group all computers used for accounting into one VLAN, all computers used for human resources into another, and so on.
VLAN Range
| Range | Description |
| VLAN 0-4095 | This range of VLAN IDs is to be used on switches. |
| VLAN 1 | This is the default VLAN of switches. It can be used, but you can’t delete or edit it. |
| VLAN 2-1001 | It is a normal VLAN range. It can be created, edited, and deleted by you. |
| VLAN 1002-1005 | These ranges are CISCO defaults for token rings and FDDI. You cannot delete this VLAN. |
| VLAN 1006-4094 | It is an extended range of VLANs. |
Moving on, let’s understand the advantages of VLAN.
Types of VLAN
The 5 types of VLAN are:
1. Default VLAN
When the switch first boots up, all switch ports are added to the default VLAN. Generally, all switches have default VLAN as VLAN 1. VLAN1 allows any network device connected to any switch port to connect with other devices on other switch ports. The VLAN1, i.e., Default VLAN, can’t be renamed or deleted.
2. Data VLAN
Data VLAN is also known as a user VLAN. The data VLAN is only used for data generated by users. This VLAN carries data only. It does not carry management traffic or voice.
3. Voice VLAN
Voice VLAN is configured to carry voice traffic. Voice VLANs typically have higher transmission priority than most other types of network traffic. We need a separate voice VLAN to save bandwidth for other applications.
4. Management VLAN
A management VLAN is used to configure the switch for management purposes. It manages system logging and monitoring. By default, VLAN 1 is the management VLAN.
5. Native VLAN
This VLAN is used to carry untagged (not belonging to any VLAN) traffic.
These are the types of VLAN.
Virtual LAN Use Cases
Some of the use cases of VLAN are:
Departmental Segmentation:
- Divide a network into multiple VLANs for different departments (e.g., finance, HR, marketing)
- Improve network organization and security
Guest Network
- Create a separate VLAN for guest users
- Limit access to sensitive areas of the network
Security
- Isolate sensitive devices or data from the rest of the network
- Prevent unauthorized access to sensitive areas
Network Organization
- Group devices by function or geography
- Simplify network management and troubleshooting
Load Balancing
- Distribute network traffic across multiple VLANs
- Improve network performance and availability
What are the Security Concerns with a VLAN?
There are several issues that need to be addressed in relation to VLAN security. Below, we have discussed some of these.
- VLAN Hopping: VLAN hopping can be defined as the action through which an attacker sends traffic onto a VLAN to which they are not authorized to access. This can be achieved by forging false packets that make the switch forward the packets on the unauthorized VLAN.
- Inter-VLAN Routing: Inter-VLAN routing enables the flow of traffic between VLANs. Sometimes, when improper configurations are done the inter-VLAN routing provides unauthorized access to restricted VLANs.
- Double VLAN Tagging: Double VLAN tagging is a type of attack in which an attacker gets authorized access to VLANs to which they should not have access. An attacker encapsulates a packet with two VLAN tags i.e., one of the authorized VLAN and another VLAN tag of the unauthorized VLAN. This way attackers get unauthorized access to VLANs.
- Broadcast Storms: Broadcast storms in a VLAN can be defined as a condition where a device floods the network with an enormous number of broadcast packets thus causing instability in the network. This can be caused by a faulty device, a misconfigured VLAN, or an attack that results in such effects as congestion, and high CPU utilization, and sometimes leads to network crashes.
Note: In order to minimize or eliminate the above-discussed security risks for VLAN, one must pay attention to the VLAN configuration and monitor the network traffic constantly. Other ways to improve VLAN security include implementing ACLs, secure trunk configurations, VLAN pruning, and encrypted communication protocols to further reduce security threats and provide a secure VLAN environment.
What are the differences between LAN and VLAN?
| Factor | LAN (Local Area Network) | VLAN (Virtual Local Area Network) |
|---|---|---|
| Latency | Higher latency due to broadcast traffic | Lower latency as it supports high-bandwidth applications |
| Network Segmentation | Physical segmentation, limited by geography | Logical segmentation, not limited by geography |
| Broadcast Traffic | Broadcast traffic is sent to all devices | Broadcast traffic is limited to the VLAN |
| Management | More difficult to manage and configure | Easier to manage and configure, can be managed from a single location |
| Security Configuration | Less secure, devices on the same LAN can access each other’s data | More secure, devices on different VLANs are isolated from each other |
| Resource Allocation | Limited by the number of devices connected to the LAN | More flexible, can allocate resources based on VLAN membership |
| Failure Domain | A single failure can bring down the entire LAN | A failure in one VLAN will not affect other VLANs |
Advantages of VLAN
- Broadcast Control – eliminates unnecessary broadcast traffic by improving network performance and scalability.
- Improves Performance by reducing the size of the broadcast domain.
- Security – logically separates users and departments, allowing administrators to configure separate security for each VLAN.
- Flexibility – removes the physical boundaries of a network, allowing a user to exist anywhere.
- VLAN solves a broadcast problem
- VLAN allows you to add an additional layer of security
These are some advantages of VLAN.
Disadvantages of VLAN
Here are some disadvantages of VLAN –
- One VLAN can leak a packet to another.
- A cyberattack might result from an inserted packet.
- A virus can infect one machine and spread throughout the entire logical network.
VLAN Ports
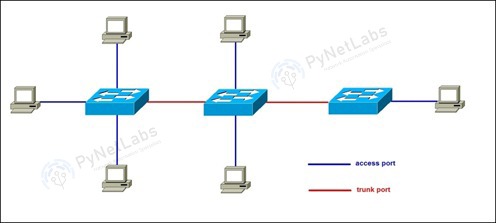
A VLAN port, also known as a tagged port or trunk port, is a network port that is configured to transmit traffic for multiple VLANs (Virtual Local Area Networks). It is typically used to connect switches or network devices together while carrying traffic for multiple VLANs simultaneously. VLAN ports add a special VLAN tag to each packet, indicating the VLAN to which the packet belongs. This allows the switches or devices to differentiate and direct the traffic to the appropriate VLANs across the network.
There are two types of ports used in VLANs –
1. Access Port
The access port is a member of only a single VLAN. By default, all switch ports on the Cisco switch are access ports. So, any device connected to any switch port becomes a member of that VLAN.
2. Trunk Port
When VLANs are configured on multiple switches, a mechanism is required to identify which VLAN a frame belongs to. This is accomplished through frame tagging, which adds a VLAN ID in each frame. These tagged frames are sent over Trunk ports.
Frequently Asked Questions
Q1. What is VLAN and why it is used?
A VLAN (Virtual Local Area Network) is a method of creating virtual networks within a physical network infrastructure. It is used to improve network flexibility, security, and performance by logically separating devices into distinct groups, regardless of their physical location. VLANs enable efficient network management and enhance overall network efficiency.
Q2. What is a VLAN with example?
A VLAN (Virtual Local Area Network) is a virtual network that allows devices to communicate as if they were on the same physical network, providing segmentation and security. For example, in an educational institution, VLANs can be set up for students, faculty, and administration, enabling separate networks while utilizing the same network infrastructure.
Q3. What are the 3 types of VLANs?
The three types of VLANs are:
- Port-based VLAN: Devices are grouped into VLANs based on the physical switch ports they are connected to.
- MAC-based VLAN: Devices are assigned to VLANs based on their MAC addresses, allowing for flexibility when devices are moved to different ports.
- Protocol-based VLAN: Devices are assigned to VLANs based on the network protocol used, such as IP addresses or specific application requirements.
Q4. Why is VLAN trunking used?
VLAN trunking is used to transport traffic for multiple VLANs over a single network link, enabling efficient utilization of network resources. It simplifies network design, reduces the number of physical connections needed, and facilitates the exchange of VLAN traffic between switches or network devices.
Conclusion
In this article, we have discussed what is VLAN, how it works, what are the different types of VLAN, its advantages, disadvantages, and range. You can Join our CCNA Training for a better understanding of VLAN. Our CCNA training is rated among the top CCNA training in India and we have also launched a free CCNA program to help all aspiring network engineers.
To conclude, VLAN is showing a promising future in the networking field and this knowledge will be beneficial for any network engineer.
If you are still with us, we are sure you have learned most things about VLAN. If you have any suggestions or feedback for us, you can comment down in the comment box. We would love to hear from you.